sara.next automates the entire access review process — from planning review cycles and notifications to generating audit reports. This enables organizations to meet SOX, ISO 27001, or NIS2 requirements without excessive workload. Full compliance and process transparency become the standard, not the challenge.
Regular access reviews are a requirement for any organization that takes information security and compliance seriously – especially under regulations and standards such as SOX, ISO 27001, and NIS2. In practice, however, this process is often time-consuming, fragmented, and difficult to oversee. sara.next was designed to automate and streamline the entire review lifecycle – from planning to results reporting – while maintaining full transparency and control.
An automated process from A to Z
In sara.next, an administrator can easily create a review schedule for any applications and roles. The system automatically:
- launches the review process according to the defined calendar (e.g., quarterly or semi-annually),
- sends automated email notifications to reviewers when a review starts,
- reminds reviewers of upcoming deadlines and escalates overdue tasks,
- generates review questionnaires tied to specific access rights,
- and, once the process is completed, produces full audit documentation ready to download as a report.
As a result, the entire review cycle runs without manual oversight, and access data remains always up to date and consistent.
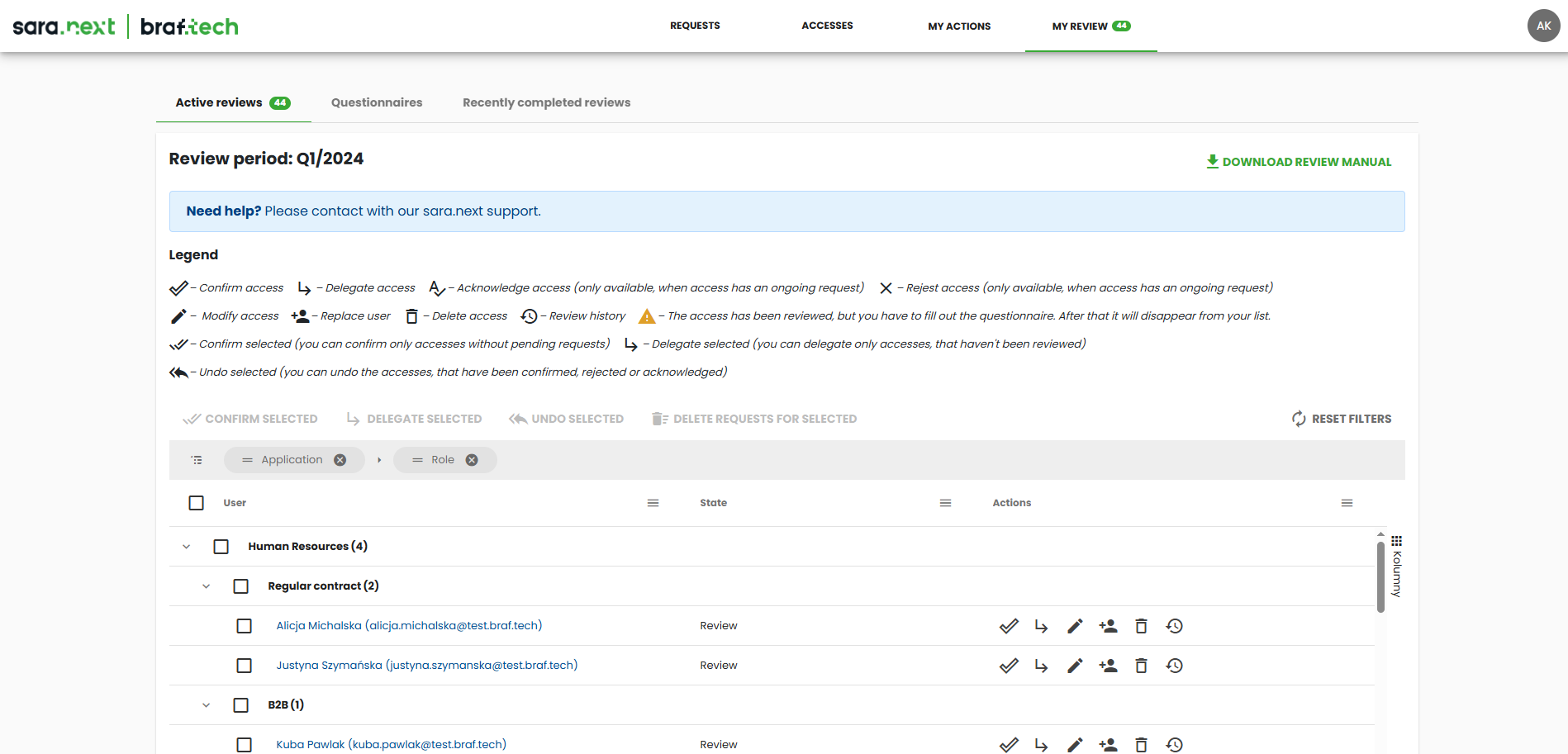
Intuitive interface for reviewers
Reviewers in sara.next get a single place where they can manage all access reviews assigned to them. For each access right, the system allows them to take the appropriate actions:
- Confirm that the access is still valid,
- Delegate the review to another user,
- Modify access, reassign it to a different user, or remove it,
- and, if needed, approve or reject pending requests.
Every action is immediately recorded in the review history and can be reconstructed during an audit. After completing a review, the reviewer fills out a short questionnaire, which becomes an integral part of the compliance documentation.
Compliance with audit requirements and SOX
The access review functionality in sara.next was designed for environments subject to SOX (Sarbanes–Oxley Act) controls, as well as UAM 6 and UAM 6.1 requirements used in listed capital groups. The review process confirms that every access right in the organization is current, business-justified, and approved by the appropriate person. The system can automatically block or remove access that is not approved within the defined timeframe, minimizing the risk of unauthorized access to data.
Full transparency and reporting
Every review completed in sara.next is archived and available in the reporting module. Administrators and auditors can generate a report at any time that includes:
- a list of users and their active access rights,
- review status,
- questionnaire results,
- and the history of reviewers actions.
As a result, an audit process that previously took weeks can now be completed in a matter of hours.
sara.next raises the bar for identity and access management. Automated access reviews not only help meet compliance requirements, but above all provide real control over who has access to what – and why. After the process is completed, the system generates complete audit documentation ready to download as a report and can automatically create access removal requests based on the reviewer’s actions.




